Your cell phone is designed to scan for available cell towers and check in with them at regular intervals. But there’s no mechanism in place in most phones to distinguish a legitimate cell tower from a fake one. "IMSI catchers," also known in the United States by the brand name "Stingray," are eavesdropping devices that mimic the behavior of a cell tower and relay messages to a real cell tower, tracking phone users and sometimes logging communication.
Ash Wilson is an engineer who has been experimenting with designs for SITCH, a device that would detect IMSI catchers. I recently worked with Ash to build a SITCH for the Open Lab.

IMSI catchers detect and identify the International Mobile Subscriber Identity information associated with a mobile phone. Because mobile phones are almost always tied to a specific person, this information can be used to monitor and track someone’s whereabouts and movement. A governmental agency with a Stingray at a political rally would be able to identify all of the cell phones in the area, and by requesting subscriber information from cell phone carriers, be able to identify en masse everyone who attended. Some IMSI catchers can also intercept and store text messages and phone calls.
According to the ACLU, over 72 agencies in 24 states possess IMSI catchers, though because of secrecy surrounding these devices, there are likely many more agencies who have them. Last week, the The Detroit News reported that IMSI catchers, ostensibly purchased by the FBI for anti-terrorism applications, were being used to hunt down undocumented immigrants.
Identifying IMSI catchers
The SITCH detector monitors three channels of information for unexpected or unusual activity: the metadata transmitted by a base station (cell towers are more accurately described as“base stations,” because not all of them are towers), the strength of the base stations’ transmission, and data from a GPS receiver in the SITCH detector.

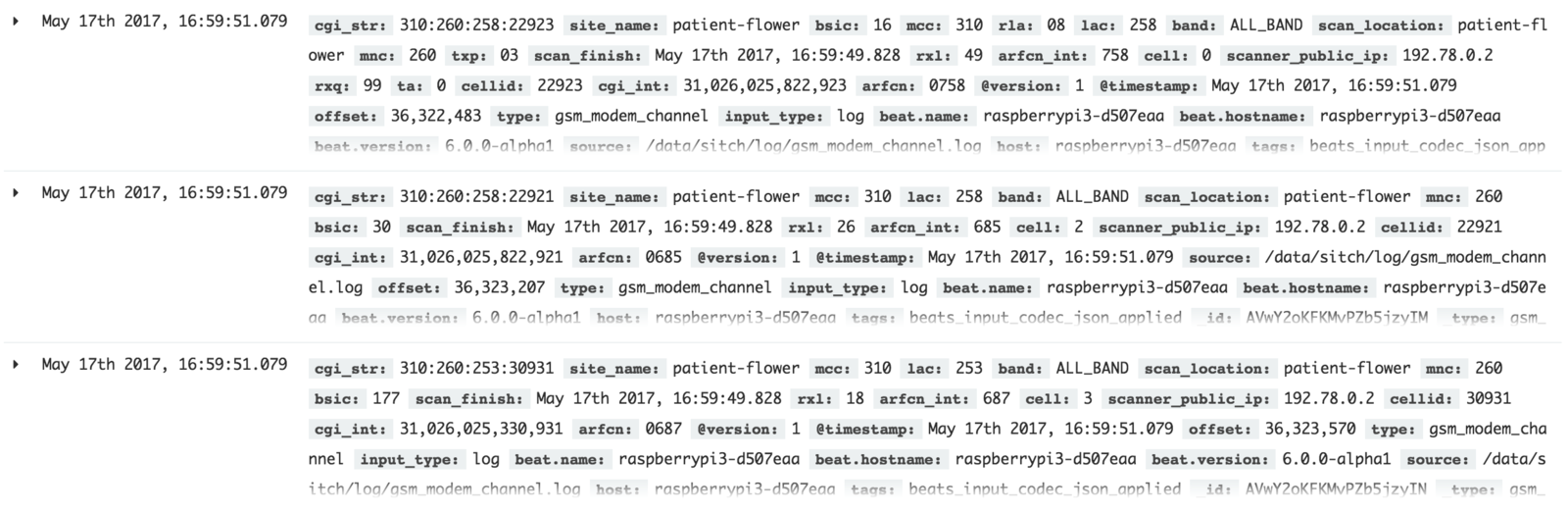
The metadata that cell towers transmit includes a unique identifier for each cell tower. The FCC’s public records are notoriously out of date, so enthusiasts have built up community sourced databases where most urban base stations are accurately recorded. If a new base station ID suddenly appears, that could also be a sign of an IMSI catcher (or, it could simply indicate a new tower being constructed.) This unique identifier includes a location code. For a legitimate cell tower, that code ought to be consistent with the location of the SITCH detector. If the location code seems to indicate an out-of-place base station, that could also be a sign that the base station is really an IMSI catcher. SITCH reads this using a standard cell modem, very similar to what exists inside of every normal cell phone.
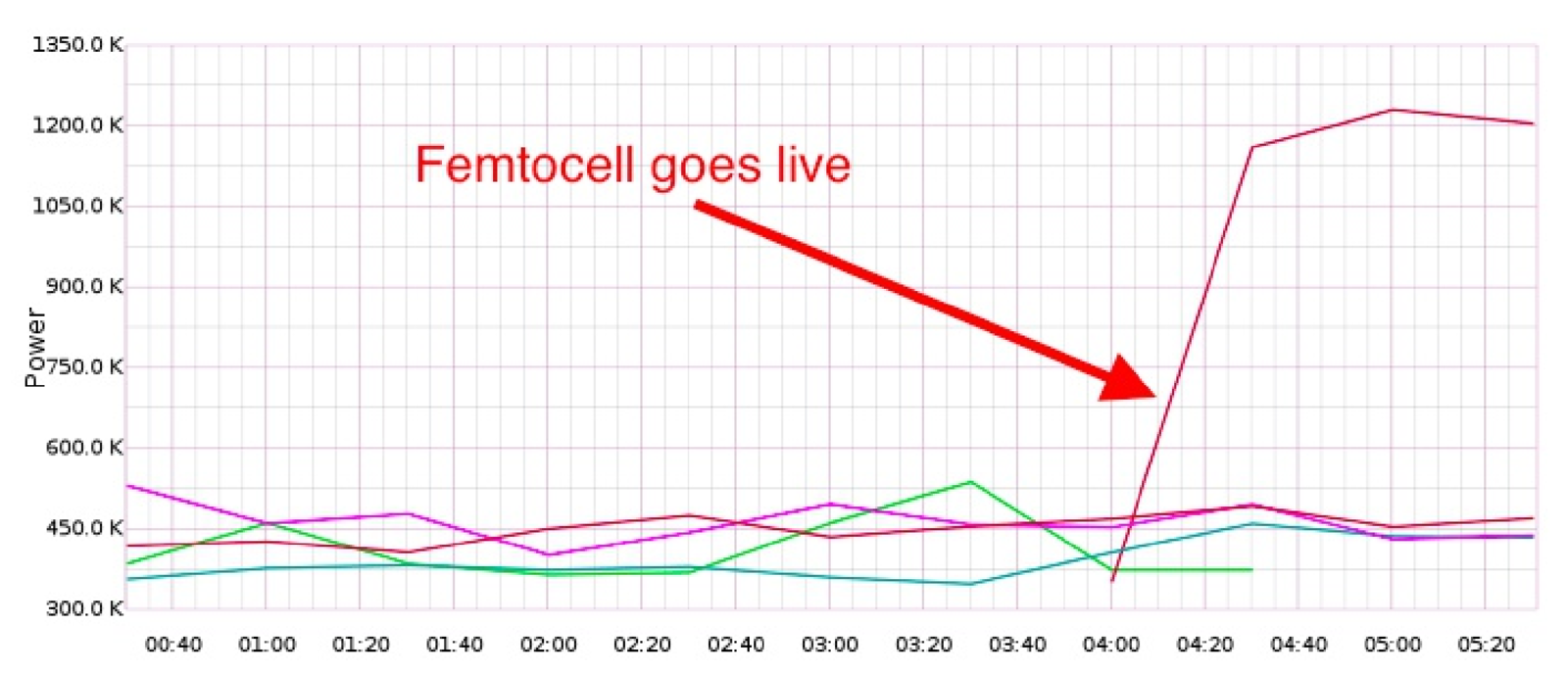
SITCH also monitors the radio spectrum in the frequency range used by cell phone base stations. IMSI catchers frequently work by using extremely high power signals that force cell phones to connect to the fake base station rather than the legitimate tower they were using previously. By monitoring the radio spectrum, SITCH is able to identify unusually high power signals.
This monitoring is performed using a software defined radio, or SDR, that can be programmed to receive signals at a particular frequency of interest. A piece of open source software called Kalibrate scans for base stations and reports the observed signal power. While Kalibrate is actually designed to use base stations as a method of precisely calibrating SDRs, SITCH uses Kalibrate as an easy way to detect base stations. However, at the Open Lab, we’ve had mixed results with this monitoring method. Kalibrate has not been able to identify the base stations that the cell modem connects to, even though they can be observed manually in the SDR software that we’re running. We’re still trying to debug this issue – the signal might be too weak inside our building to be accurately picked up by a non-specialized radio.
In addition to the radio monitor, SITCH also has a GPS receiver, for two reasons. The SITCH’s latitude and longitude, combined with the crowdsourced cell tower database, helps confirm that base stations observed by SITCH’s cell modem are base stations that are supposed to be nearby. SITCH also monitors GPS drift and compares the GPS time with the the system time to guard against esoteric, but theoretically possible GPS spoofing attacks.
SITCH reports its observations to a web server, where data can be logged and graphed in dashboards. Unexpected measurements trigger alarms via Slack. A network of similar DIY logging stations could be deployed across a city, and the combined data could be used to keep track of when and where IMSI catchers are being deployed — important information for anyone who values security and privacy while using a cell phone. Our SITCH isn’t working perfectly yet, but we’ll get there. Until regulation forces transparency around their use, citizens can track IMSI catchers themselves.

Open Lab for Journalism, Technology, and the Arts is a workshop in BuzzFeed’s San Francisco bureau. We offer fellowships to artists and programmers and storytellers to spend a year making new work in a collaborative environment. Read more about the lab.
