
Campaigners and security researchers in the UK have warned that the prosecution of Marcus Hutchins – the researcher who helped stop the WannaCry ransomware attack that took down National Health Service computers – could damage their relationship with US law enforcement agencies and leave the country more susceptible to attack.
British supporters told BuzzFeed News that the type of work done by Hutchins and fellow security researchers often took place in legal grey areas and so relied on a relationship of trust with law enforcement agencies. Those relationships, they said, had been put under strain by his arrest.
"It can only harm the willingness of security researchers like Marcus to work closely with the authorities and certainly to be named and to step out of the shadows," said Naomi Colvin of the whistleblowers' group the Courage Foundation, who also told BuzzFeed News that Hutchins had done work with the UK's National Cyber Security Centre (NCSC).
"We should be embracing this community of researchers and fostering their efforts, encouraging them and congratulating them where things have significant positive public impact like Marcus had in stopping the WannaCry malware when he did," she said.
Hutchins, generally known online as MalwareTech, was detained on 2 August as he prepared to board a flight back to Britain from a security conference in Las Vegas. He was charged with six counts related to allegations he helped prepare and sell malware, along with an unnamed codefendant.
Hutchins is currently on bail and barred from leaving the US, but has pled not guilty to all six charges. At a hearing in Wisconsin on Monday, he was granted permission to access the internet once again, having been barred at a previous bail hearing.
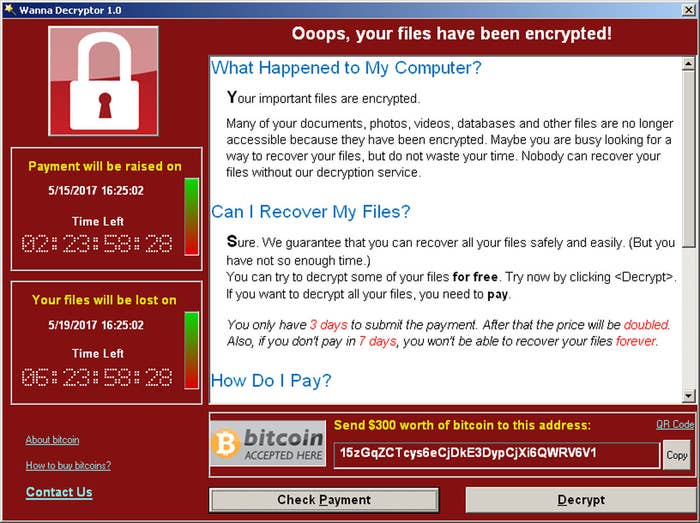
He came to public prominence in May, shortly before the US conference, as the researcher who found the "kill switch" in the WannaCry malware, which had until then been rapidly spreading through institutions across the world. Britain's NHS was badly hit, damaging diagnostic equipment and leading to wards being shut.
Hutchins found a temporary fix to stall the spread of the malware – which was created in part using hacking tools developed by the CIA that had publicly leaked – buying time for permanent solutions and restricting the damage it caused.
Attendees at a UK meeting for Hutchins last week also highlighted several unusual factors in Hutchins case, including:
– The brevity of his indictment – a mere eight pages – when cybersecurity charges often run to hundreds of pages of evidence.
– The fact that the charges came from the US attorney for the Eastern District of Wisconsin, rather than the Southern District of New York, which usually handles high-profile hacking cases.
– And the fact that Hutchins was detained during a visit to the US two years after the alleged criminal activity, with no mention of whether extradition had previously been sought from the UK.
wann
Colvin said that even respectable researchers like Hutchins often operated in legally grey areas for the public good.
"There’s a lot said about 'black hats', 'white hats', 'grey hats' – this is the cliche in this field you always hear from hackers," she said. "My take is it’s not the practice that is morally grey but that the law doesn’t distinguish clearly enough between things which are a problem and things we need to make the internet safer."
Colvin said the case also raised questions for the relationship of trust between UK authorities and the independent researchers they often rely on.
"The danger this is going to harm the goodwill and mutual trust which exists between independent researchers and the authorities. I would certainly understand if people became reluctant to travel to the United States off the back of this, and I really think it damages the reputation of UK law enforcement in this area," she said.
"Marcus is a British citizen. There is a real question of whether UK authorities knew what was about to transpire, and if they did they have a duty of care towards Marcus who has been working with the NCSC in protecting British citizens and those across the world online."
Colvin's comments – and her concerns that charges could send security researchers back into the shadows – were echoed by two security researchers also present at the event.
"It’s important to say the vast majority of security researchers are absolutely trying to prevent harm, rather than cause harm," one security researcher who described himself as a friend of Hutchins, but asked not to be named, told BuzzFeed News.
"The best way to achieve that sometimes if highlighting where there are vulnerabilities, issues, weaknesses or challenges with systems that could lead to them being compromised. Writing this type of code that can highlight these weaknesses helps ensure they can be tested and made safe against these attacks."
The researcher said the information security community was now publicly debating fears around working with – let alone travelling to – the US, which could pose risks to keeping the internet secure.
"If this is a risk that can occur, why would you travel over there and expose yourself to that risk," he asked. "And there are concerns beyond just traveling there, even just working with and trying to help the US there’s been calls about people being discouraged from working with law enforcement and intelligence agencies …
"But even in this case with the US, there are people saying we’re concerned about sharing with them because it might come around full circle and cause us all kinds of legal issues down the road."
Another researcher present at the event – who asked not to be named because he did work with UK military and law enforcement – said UK law did better to distinguish between those with good and bad intentions.
"In UK law, there’s a position about intent – so holding a set of lock picks, for instance, without intent is perfectly legal," he explained. "Holding a set of lock picks with the intent to break in somewhere is the offence. So you can develop code with no intent of actually using it unlawfully."
By contrast, he added, several US laws worked differently, leaving researchers no option but to commit technical offences and rely on prosecutors to use their common sense.
"So if you’re doing security research and you’re breaking [say] a Digital Rights Management tool, in the US that’s an offence and it’s a very strict liability," he said. "So you’re always going to be in those grey areas. … In every common law society, intent is defined by the prosecutor, it’s not codified."
Elsewhere in the event, lawyer Karen Todner – who has represented people in multiple high-profile cyber-related extradition cases – suggested her advice to Hutchins' family would be to strike a deal that allowed him to return to the UK, owing to the high costs and risks of proceeding to trial.
"If I were a member of his family my priority for him would be to get him back to the UK as quickly as possible," she told the assembled attendees. "Ninety-eight per cent of people in the US take a plea agreement.
"If you stand trial in the US your sentence can be six or seven times more than it is if you take a plea agreement, so if you stand trial and you’re found guilty you can look to go to prison for a substantial period of time compared to if you just take a plea agreement.
"If I, again, were a member of his family I’d be thinking you need to take a plea agreement, preferably with a noncustodial sentence, but if there were a custodial sentence with the consent of the prosecutor to allow him to be returned to the UK fairly immediately."
Hutchins' US lawyer, Marcia Hofmann, told reporters he planned to "vigorously defend himself" against the charges and would be "fully vindicated" at trial.
