There’s a worrying trend emerging when it comes to keeping our personal information safe online. Hackers have begun to identify our smartphones as a better target than the PCs and laptops we’re accustomed to defending with anti-virus software.
Smartphones are the target of choice for malware, and with the plethora of information we habitually store in our devices, it’s little wonder why mobile malware attacks doubled last year.

Today, we use our mobile devices to make purchases, track our GPS, store an array of passwords for social media and shopping platforms, and, of course, to make telephone calls. All such information is up for grabs in the eyes of hackers, and it’s primarily through the implementation of malware that they can access such sensitive data.
Malware essentially infiltrates your phone in a way that enables attackers to see your personal information as well as take pictures and record audio without any prior permission. Typically, smartphones can be infected through trojan applications posing as major apps like WhatsApp, malicious spam emails, unsecured WiFi spots and via out-of-date software.
Luckily, there are plenty of measures you can take in ensuring that your smartphone is as safe as can be from prying eyes. Here’s a look at five of the most effective forms of security that you can adopt for your device:
Keep updated and take precautions
As mentioned before, it’s imperative that you keep your mobile phone updated and don’t ignore operating system updates.
While this may seem like second nature to some, many users have been put off of updating their handsets following the revelation that both Apple and Samsung had been found to be deliberately slowing down their devices in a bid to encourage purchases of their newer models.
While some users fear the sight of the ‘update ready to install’ notifications we all receive, many of the downloads that Apple and Android devices undertake are designed to efficiently patch up any exposed security flaws. Ignoring the prompt to update your device leaves said flaws exposed for hackers to exploit.
It’s also highly recommended that you utilise the security features available for your smartphone. You may find the use of passcodes to access your phone a nuisance, but that added layer of protection can help to ensure your privacy - all for the sake of an extra three seconds each time you look to browse your device.
Modern smartphones have gone one step further and feature biometric security like fingerprint sensors and facial identification. Again, if your phone is compatible with biometric identification features, it can pay dividends if you take the time to set yourself up with an added layer of protection.
Use your app store responsibly
Fake apps are an increasing problem for both iOS and Android users, with some gaining over eight million downloads on the Google Play store alone. The instances of fake apps appearing available for download is increasing exponentially, with six times as many harmful programs cropping up in December 2018 as there were in June of the same year.
Many fake apps act as trojan malware that aims to underhandedly gain access to as much of your personal information as possible. While it can be difficult to ascertain what’s real and what’s not on smartphone app stores, there are some useful measures to take to ensure that you’re as safe as can be when looking for your next addictive game to play for that upcoming long-haul flight.
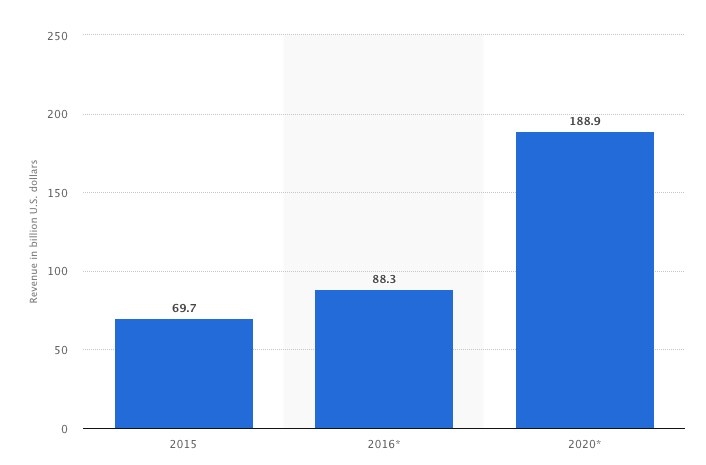
As a result of consistent mobile app revenue growth, there’re more opportunities for hackers to take advantage of its popularity.
Firstly, steer clear of third-party app stores. If you can’t find the application you’re looking for in an official store, then there could well be a good reason why. It’s also important to double-check the name of an app’s developer before you click to download it to your device. If the name of the developer in question doesn’t look right, it could be worth consulting Google for corroborating evidence.
Another strong measure you can take is to have a look at the app’s user reviews. If an app has an unusually low number of reviews or if some reviewers accuse the program of being malicious, it should be treated as a red flag.
Switch to a secure smartphone network
If your smartphone has been the subject of repeated attacks, or if you’re tasked with storing strictly confidential material on your device, it could be worth investing in a highly secure cellular network.
Irbis Network (SafeCalls) is an example of such a network. A decentralised blockchain-based telco network that offers the ability to anonymous connection, random routing, voice change and MSISDN hiding.
Get LogDog
It’s important to keep your processes in check behind the scenes, and with LogDog you can make sure that all of your identities across existing apps are safe and secure at all times.

LogDog monitors your identity on platforms like Facebook, Gmail and Dropbox, and is tirelessly on the lookout for suspicious activity and evidence of brute force entries into any accounts you have stored on your smartphone. LogDog even has the ability to keep on the lookout for sensitive material within your email inbox and outbox - providing prompts in case it finds anything like exposed bank details or account passwords.
Use a password manager
The problem with passwords is that there’s just so many of them to keep track of. We all know that short and snappy passwords are susceptible to being guessed by hacking technology, just like we’re well aware that long and varied passwords are difficult to keep track of.
Luckily, password managers are on hand to keep even the most difficult of your codes in check so you don’t have to worry about writing down your sensitive information in a bid to jog your memory later on.
KeePass is an example of a great open-source password manager. Instead of having to remember a plethora of complex passwords, enjoy the freedom of only having to make a mental note of one.