
Cyber attacks on a major host that correctly routes internet users to websites caused widespread service outages Friday, including for Twitter, Spotify, and Reddit.
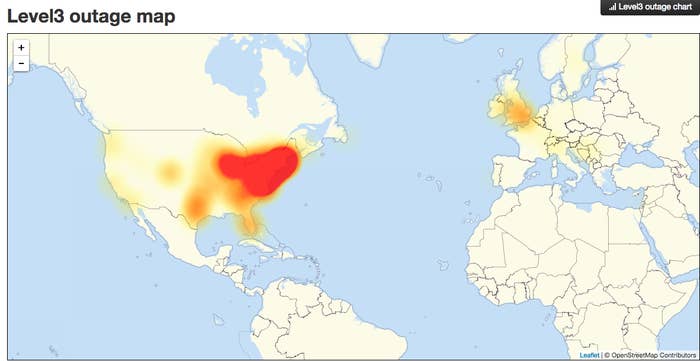
The massive Distributed Denial of Service (DDoS) attacks on the servers of Dyn began as the east coast was waking up, and then, just as internet service began to resume, appeared to hit again as the west coast awoke. Dyn said services were restored to normal after the first attack as of 9:42 am ET. Dyn was investigating another attack at 11:52 am ET. And as of Friday afternoon, the company said engineers were continuing to "investigate and mitigate several attacks" aimed at its infrastructure.
A DDoS attack overwhelms a company's servers with traffic from multiple sources to make online service unavailable. DNS, or Domain Name System, is the internet's system for converting alphabetic names of websites — the ones humans use — into machine-friendly IP addresses, which direct users' internet connection to the correct website. By attacking a DNS host, such as Dyn, they are essentially attacking the internet's ability to route users to the correct webpage.
Speaking on CNN, Rep. Adam Schiff, the top Democrat on the House Intelligence Committee, said US officials were still trying to determine who was responsible for the DDoS attack.
The FBI is also investigating the cause of the attacks, a law enforcement source told NBC News and Reuters.
"Obviously, the Department of Homeland Security is looking deeply into this, it is of great concern, but at this point it's too early to say what was the cause of this, who was responsible and what the motivations may be," Schiff said. "A lot that we don't know about just how this took place, but if it was a cyber-attack I'm confident with the forensic capabilities that we have, well get to the bottom of where it came from, and then figuring out the why of course is also of vital importance."
Reuters reported that the White House had asked "US authorities" to monitor the cyber attack.
Brian Krebs, a cybersecurity expert whose own site was brought down by a DDoS attack last month, wrote that the attack on Dyn came just hours after the company's senior researcher, Doug Madory, had presented a talk on DDoS attacks at a meeting of the North American Network Operators Group (NANOG). The talk included research Madory and Krebs had published together on how cybercriminals were involved in DDoS attacks.
"Spreading the DDoS Disease and Selling the Cure examined the sometimes blurry lines between certain DDoS mitigation firms and the cybercriminals apparently involved in launching some of the largest DDoS attacks the Internet has ever seen," wrote Krebs on his blog. "Indeed, the record 620 Gbps DDoS against KrebsOnSecurity.com came just hours after I published the story on which Madory and I collaborated."
A statement on Dyn's website said:
Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time.
This attack is mainly impacting US East and is impacting Managed DNS customer in this region. Our Engineers are continuing to work on mitigating this issue.
Other websites affected by the attack included Netflix, PayPal, SoundCloud, Etsy, Zillow, Shopify, Reddit, Github, and Pinterest.
Cybersecurity expert Bruce Schneier, who wrote a blog post earlier this year called "Someone is Learning How to Take Down the Internet," said a number of calibrated attacks have been testing the backbone of the internet of several years.
"Recently, some of the major companies that provide the basic infrastructure that makes the Internet work have seen an increase in DDoS attacks against them. Moreover, they have seen a certain profile of attacks. These attacks are significantly larger than the ones they're used to seeing. They last longer. They're more sophisticated. And they look like probing," Schneier wrote. "One week, the attack would start at a particular level of attack and slowly ramp up before stopping. The next week, it would start at that higher point and continue. And so on, along those lines, as if the attacker were looking for the exact point of failure."
Schneier, who spoke with BuzzFeed News about the blog post, said he was unable to give details about the companies being affected.
This is a developing story. Check back for updates and follow BuzzFeed News on Twitter.

