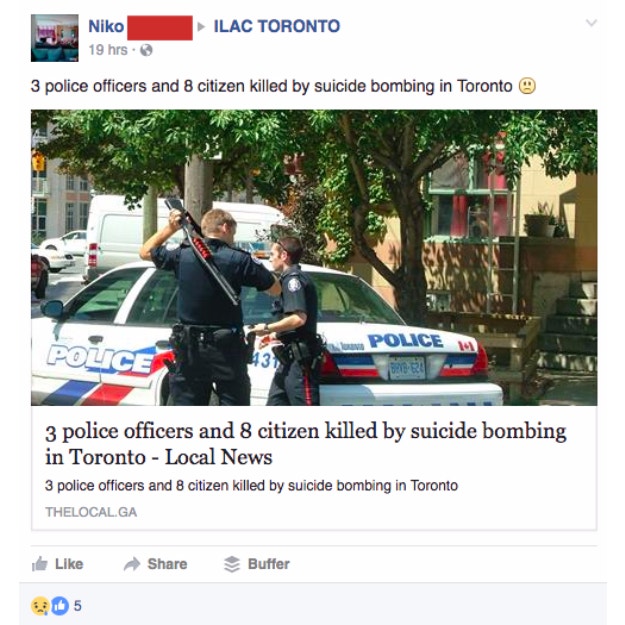
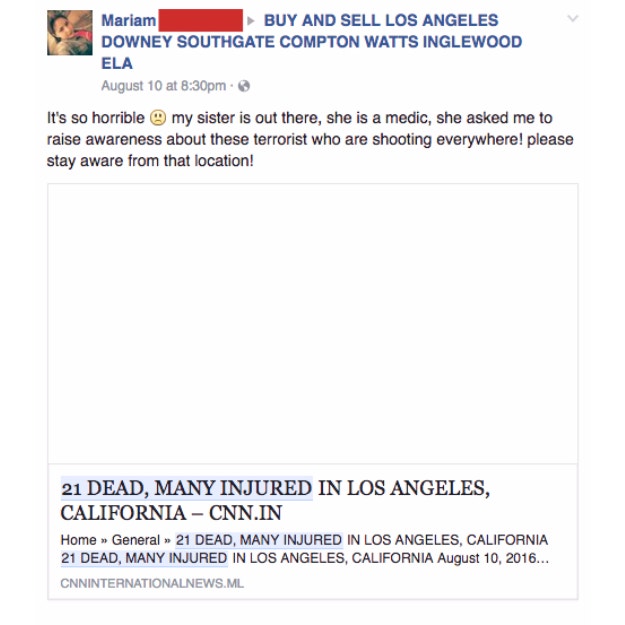
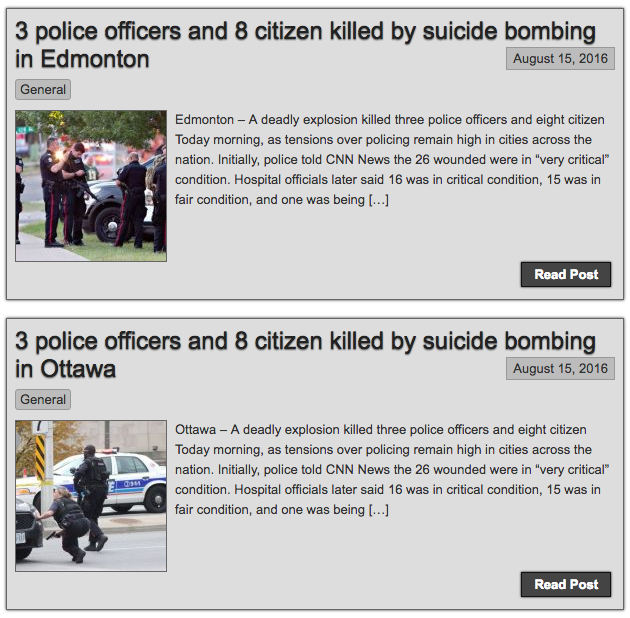
This week police in Ottawa issued a warning to the public about hoax news articles that claimed there was a terrorist attack in the region. Police shared two images of fake news stories posted on Facebook:
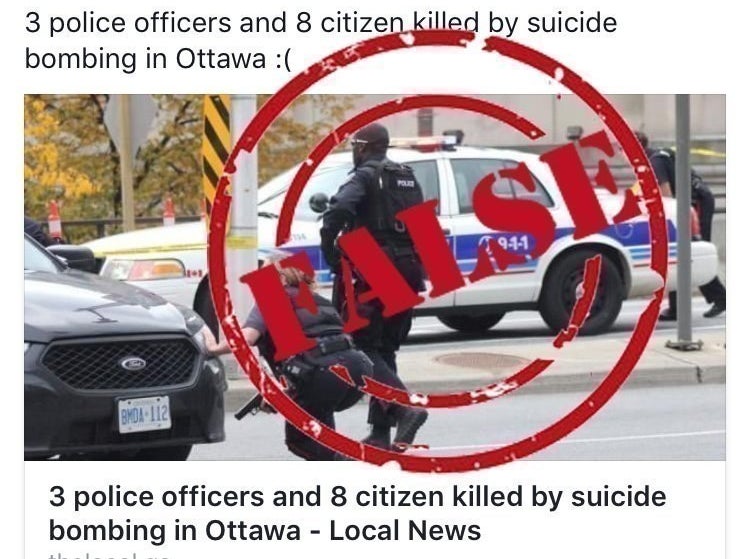
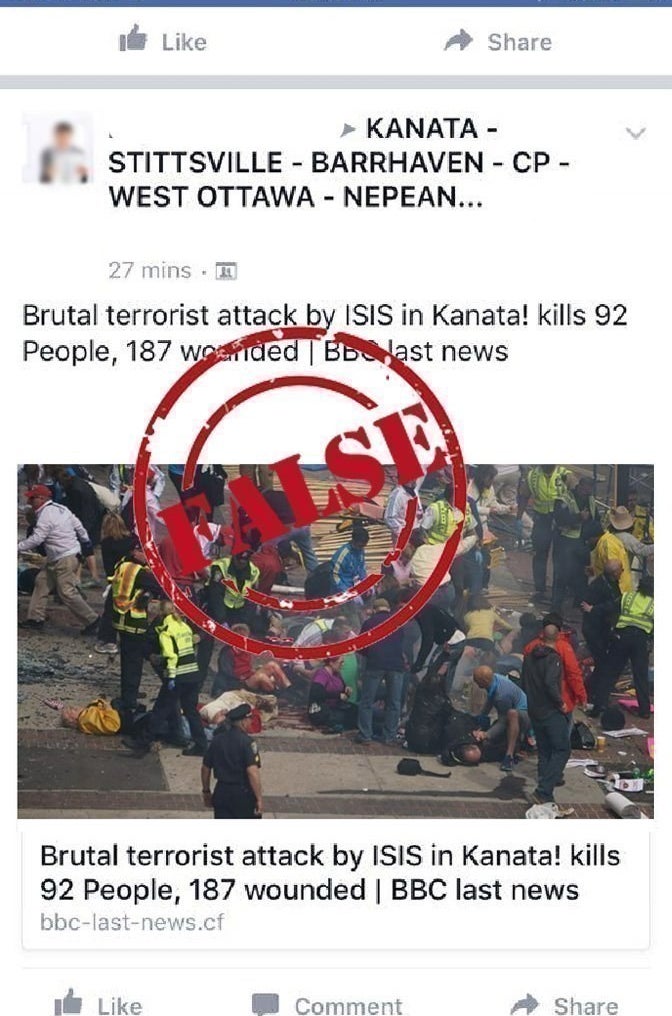
One hoax claimed three officers and eight citizens had been killed in a suicide bombing in Ottawa. The other, from a different website, claimed an attack by ISIS in the suburb of Kanata had killed 92 people and wounded almost 200 others.
Both hoaxes were posted in private Facebook groups for people in the local area.
The last few weeks have in fact seen a rash of these fake local ISIS attack stories. The articles come from websites with domains that are similar to legitimate news organizations: CNNInternationalNews.com, CNNInternational.tk, HeraldNews.tk, and CBCNews.gq.
These hoaxes appear to have started in late 2015, when they targeted places in the UK. They spread enough that local police spoke out to warn the public.
So, who's behind this coordinated effort to drive traffic to dubious websites using hoaxes about terrorist attacks? And why are they doing it?
An investigation of domain ownership records, of website source code, and of the people who have played a key role in spreading these hoaxes reveals a strong link to people in the country of Georgia.
Their goal is to use the hoaxes to get people to go to websites where they do one of three things: infect the user's computer with malware, trick people into handing over personal information, or redirect the traffic to online gaming sites in order to earn a commission. (It's important to note that while people in Georgia are playing a role in this scam, the ringleader(s) may be located elsewhere.)
This is the strange story of how two seemingly random recent hoaxes about communities in Canada can be traced back to the former Soviet republic of Georgia, and to a business that uses frightening hoaxes about ISIS to make money.
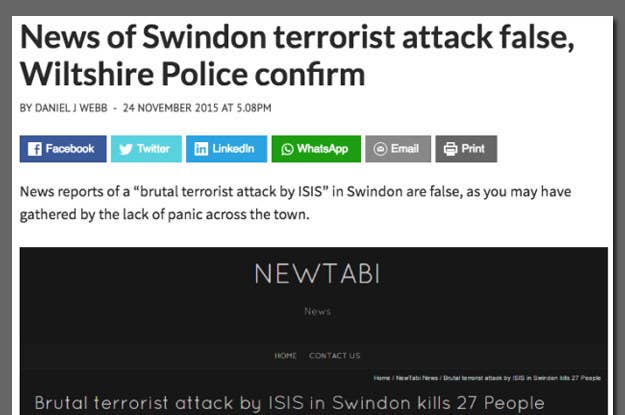
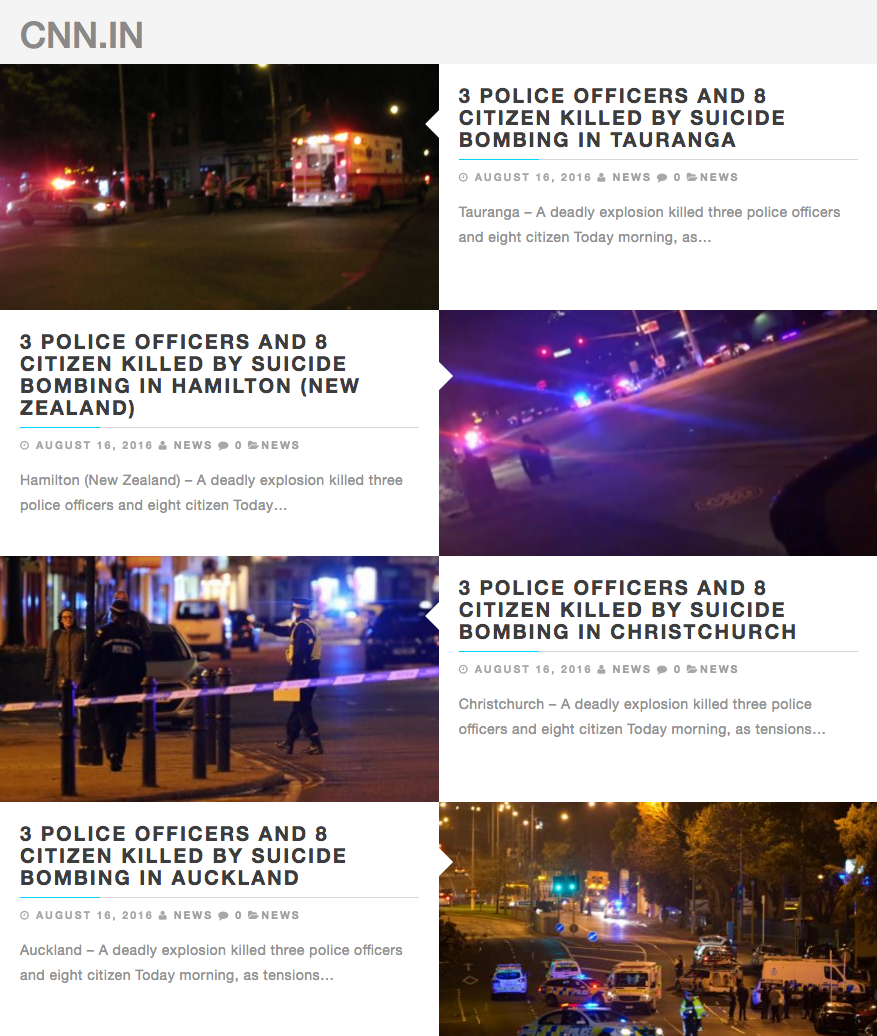
The website that hosted the Ottawa attack hoax is still online at TheLocal.ga. Its homepage is filled with copies of the same hoax bombing story, each with different city names.
Both sites have kept their domain ownership records private. However, a Google search found that a website, CNNInternationalnews.com, used the exact same headline and body text as TheLocal.ga in hoax stories about places in New Zealand.
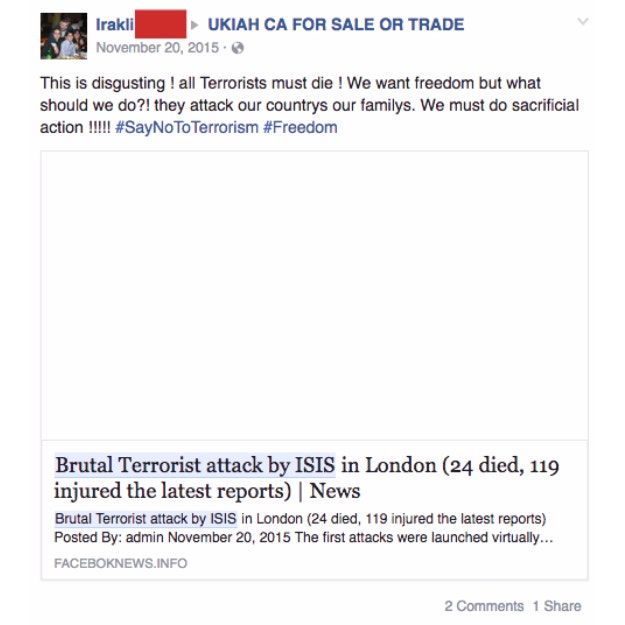
The headline text of the other fake Canada attack story has also been used by other websites. A search of "brutal terrorist attack by ISIS" on Facebook brought up the UK police warnings about the hoaxes from back in November and December 2015.
Hoax articles circulating social media reporting 'terrorist attacks' in parts of Cheshire. This is NOT true..(1/2)
Some of the domains running that hoax included ReportForLife.com, BrutalEng.com, NewTabi.com, World-BBC-News.com, BBC-Breaking-News.gq, AllCrashNews.com, FacebookNeww.info, DailyMirror.cf, and UnblockedGames.eu.
As with the fake BBC website, seven of those domains listed owners in Georgia. BuzzFeed News emailed all of the publicly listed owners seeking comment, but none have responded.
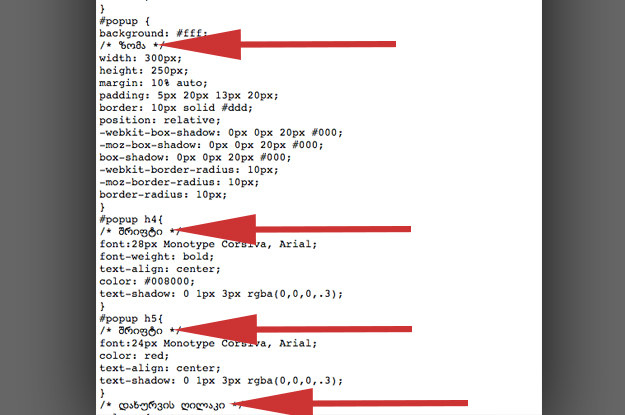
One site, BBC-Breaking-News.gq, hid its domain ownership record but had source code that included comments in Georgian. This suggests the programmer or designer who helped customize the site is Georgian.
Along with being listed as the owners of the hoax sites, Georgians have played a key role in spreading the hoaxes. One of the screenshots shared by Ottawa Police showed someone named Sopo Khotivrishvili sharing a hoax in an Ottawa Facebook group.
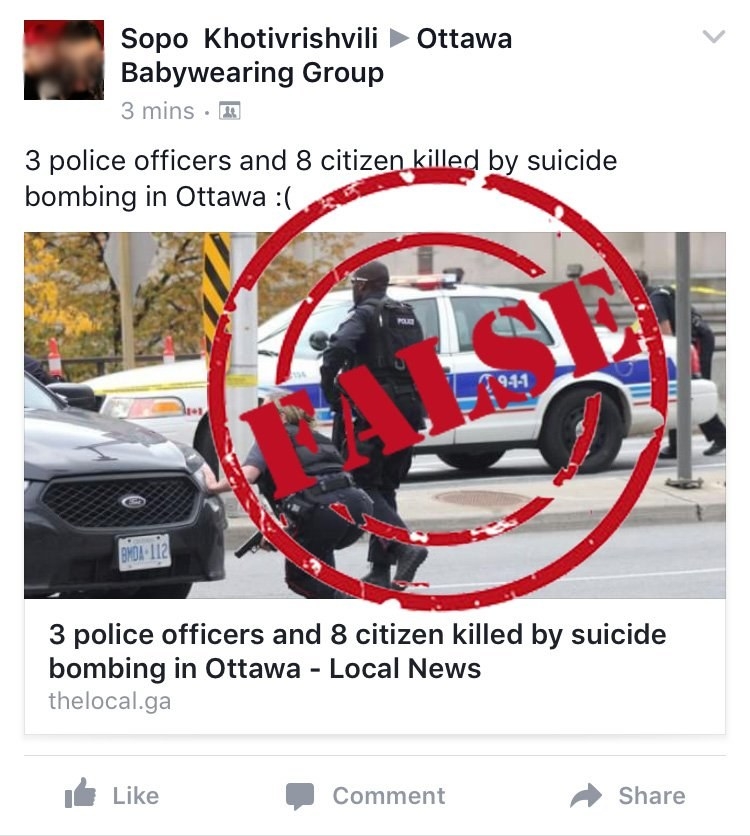
The account's current profile and cover photos show members of the band Twenty One Pilots. Those pictures were changed in late July, right around the time this latest burst of hoax attack stories started spreading again.
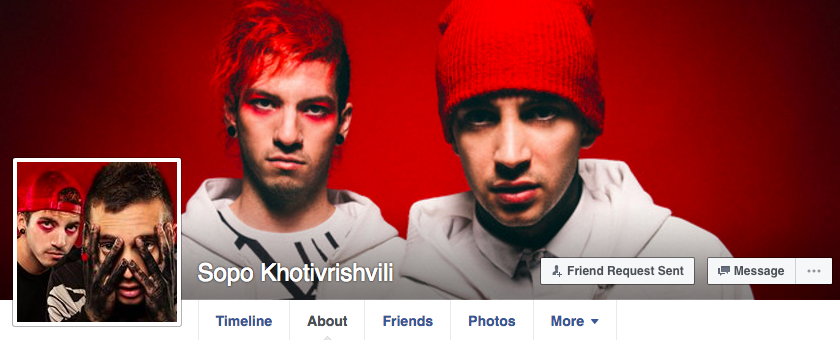
Prior to that change, the account mostly posted photos of a family in Georgia, and of a young girl in particular.

For example, this Georgian shared a hoax about an attack in Philadelphia in a Facebook group about the TV show It's Always Sunny in Philadelphia.
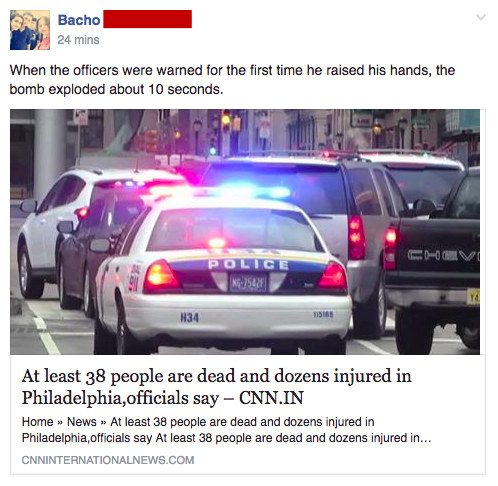
Though just about everything this person posts on his profile is in the Georgian language, and all of his friends are in Georgia, his profile says he lives in Philadelphia and that he was born there, too.
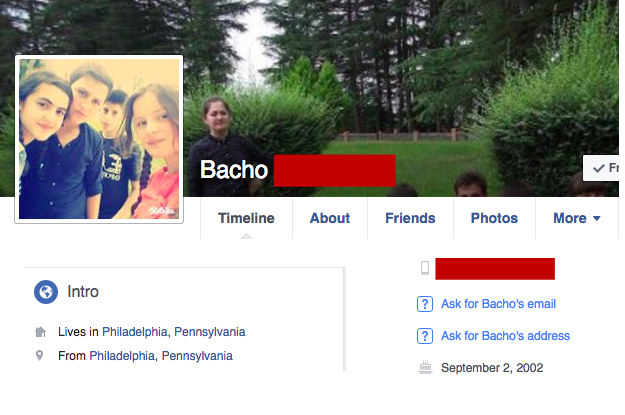
Since we were now Facebook friends, I was able to watch as this account joined one Philadelphia Facebook group after another so it could keep sharing the hoax.
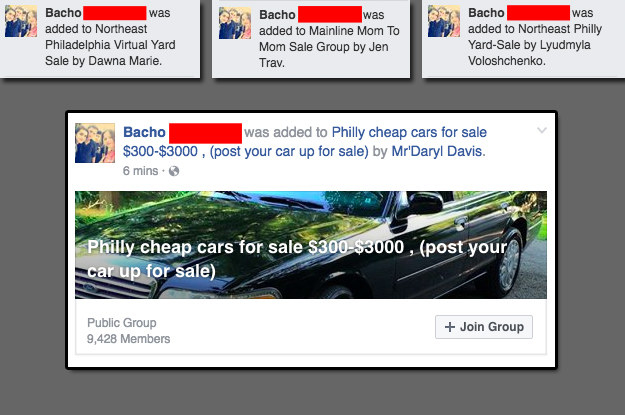
It's a pattern. Here are six other examples of Georgian accounts posting hoax terrorist attack articles in Facebook groups to help them spread (click on the city names to see each example):
That's how the hoaxes spread and drive traffic to the websites. But how do the people running these websites make money?
As noted earlier, some sites trick visitors into downloading malicious software, or they do their best to get readers to hand over personal information.
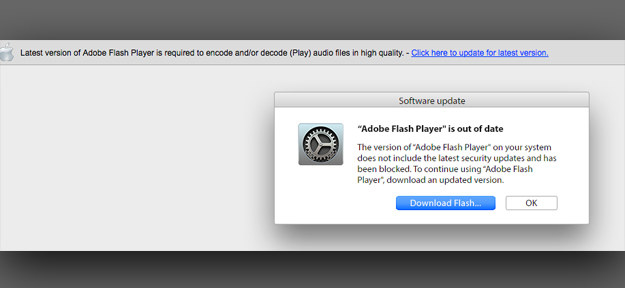
The other way at least one of these sites made money was by sending its traffic to online gaming sites. BBC-Breaking-News.gq had a pop-up ad that sent the user to one of several gaming websites, such as this one.
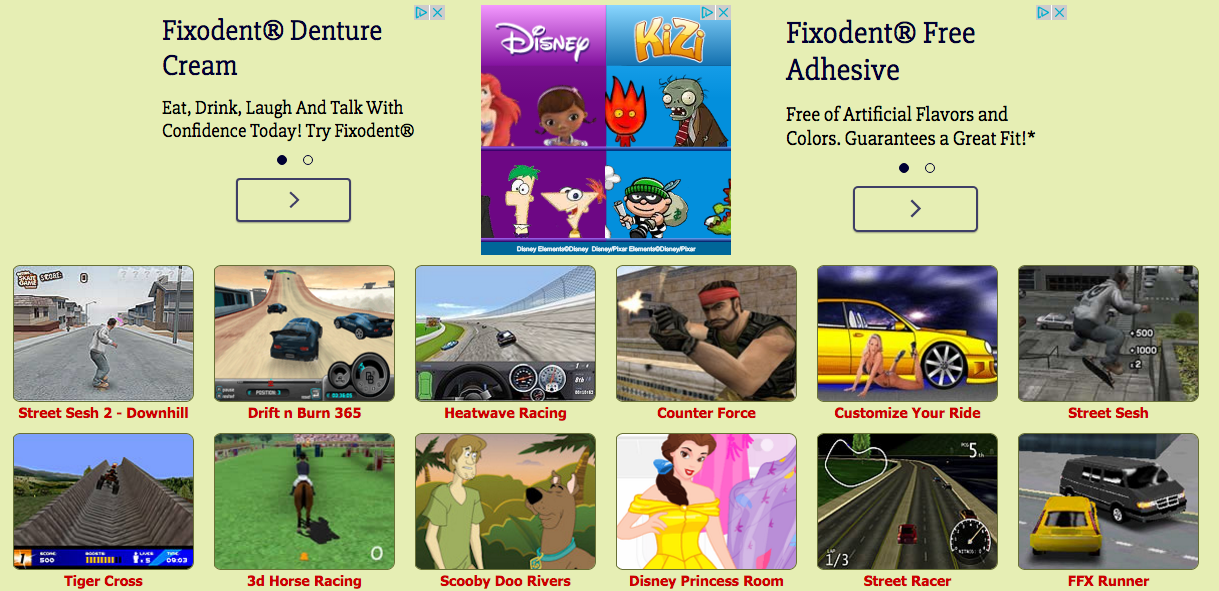
These strategies are apparently profitable enough to motivate the Georgians — or whoever is employing and/or hacking them — to run the hoax ISIS attack scam again and again. Even when local police catch on, they tend to just warn the public and not investigate.
A spokesman for Ottawa police told BuzzFeed News that they are not pursuing the hoaxers.
"It's happened before over the years and it's nothing we haven't seen before," he said.
The international nature of the operation also makes it tough for local police to stop this, even if they were inclined to investigate.
And that means this scam will keep running.
To review, here's how the hoax/scam works:
* Someone or several people create websites filled with copycat articles about terrorist attacks in different cities and towns.
* They hack existing Facebook accounts, create fake ones, or enlist real people to help them spread the articles.
* These Facebook accounts change the location listed in their profile to align with the location of the hoax they plan to spread.
* They find Facebook groups centered around the location and request to join.
* Once approved, they share the hoax article in the group, hoping that this will cause the hoax to spread among people in the community.
* People click on the link and visit the website, where they are shown a pop-up ad that pushes them to download malware, to share their personal information, or that will send them to a website that pays a commission back to the scammer for the traffic.
* When the websites running the hoaxes get shut down due to copyright infringement claims from media companies or as a result of law enforcement action, the scammers registers new domains.
* Repeat.