
Researchers at Codenomicon and Google Security have uncovered a massive security flaw, which can be exploited to steal passwords, usernames, information, and secret keys. The flaw has been found in recent versions of the cryptographic software library, OpenSSL, which protects the privacy of information transmitted across the internet. It's been named the "Heartbleed Bug."
The flaw has been described by security experts as a "serious vulnerability," given that Open SSL technology runs encryption for two-thirds of the internet. Users will recognize SSL-encrypted sites by the padlock icon that appears next to the address in your browser.
Here's the description from Codenomic's dedicated Heartbleed page, Heartbleed.com (emphasis ours):
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
According to the internet security company Netcraft, around 500,000 sites are currently vulnerable to Heartbleed.
The heartbeat extension was enabled on 17.5% of SSL sites, accounting for around half a million certificates issued by trusted certificate authorities. These certificates are consequently vulnerable to being spoofed (through private key disclosure), allowing an attacker to impersonate the affected websites without raising any browser warnings.
Throughout the day, developers have been finding vulnerabilities that allow attackers to scrape data like usernames and passwords.
Seriously, Heartbleed is fucking catastrophic: here’s a script to extract cookies from vulnerable HTTPS servers: https://t.co/app5XV81Is
Earlier Tuesday, Yahoo was found to be vulnerable, along with OkCupid. These appear to be the biggest sites affected by the flaw (so far).
Do not login to Yahoo! The OpenSSL bug #heartbleed allows extraction of usernames and plain passwords!
I don't get why Yahoo wouldn't fix this OpenSSL bug earlier. Akamai, Cloudflare, others, seem to have gotten heads up in advance.
However, Yahoo confirmed to CNET this afternoon that the flaw was patched.
As soon as we became aware of the issue, we began working to fix it. Our team has successfully made the appropriate corrections across the main Yahoo properties (Yahoo Homepage, Yahoo Search, Yahoo Mail, Yahoo Finance, Yahoo Sports, Yahoo Food, Yahoo Tech, Flickr, and Tumblr) and we are working to implement the fix across the rest of our sites right now. We're focused on providing the most secure experience possible for our users worldwide and are continuously working to protect our users' data.
As reported by Digg, Google has applied a patch to the service.
The security of our users' information is a top priority. We proactively look for vulnerabilities and encourage others to report them precisely so that we are able to fix them before they are exploited. We have assessed the SSL vulnerability and applied patches to key Google services.
Timothy B. Lee at Vox got confirmation that Microsoft is monitoring the situation:
"We are following reports of an OpenSSL library issue. If we determine there is an impact to our devices and services, we'll take necessary steps to protect our customers."
Yahoo-owned Tumblr notes it hasn't been breached, but urges users to remain vigilant:
This might be a good day to call in sick and take some time to change your passwords everywhere — especially your high-security services like email, file storage, and banking, which may have been compromised by this bug.
The official Heartbleed site has created a test page where you can enter specific URLs to see if they're vulnerable to the flaw.
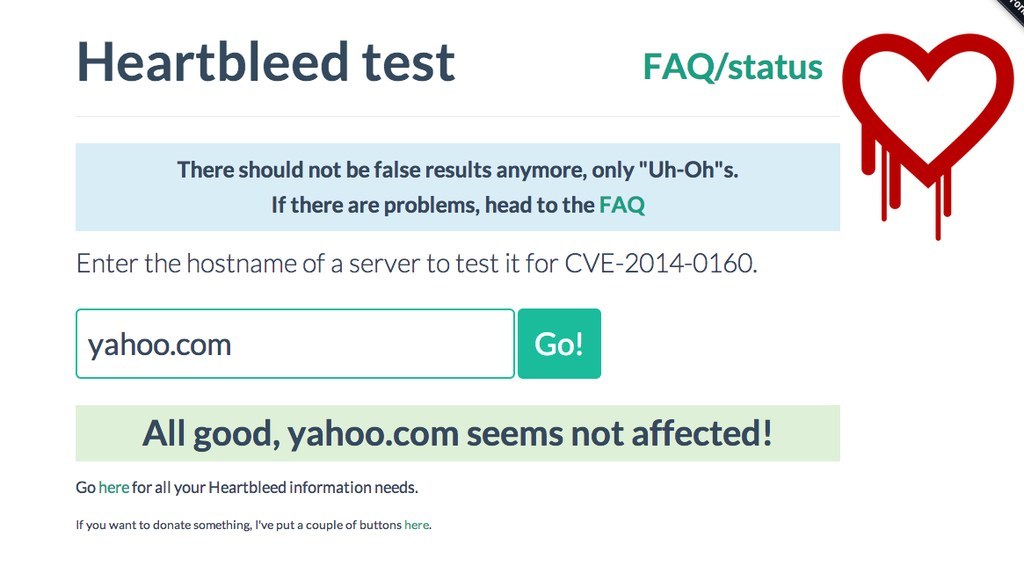
Are you at risk? And what can you do?
Everyone is potentially at risk and there's a decent chance you'll be changing at least some of your passwords this week. Unfortunately, there are no easy, blanket ways to tell if you've been affected by visiting a vulnerable site. CNET has a fantastic primer on 'How To Protect Yourself' which you should read in its entirety. However, users should make sure to change passwords on affected sites once patched and actively monitor any financial statements to be safe if you believe an account could be compromised.
