WASHINGTON — There are now more than 5,000 social media accounts operated by the federal government, spanning departments, agencies, and public officials, and delivering information directly to U.S. citizens and beyond.
But the security for these accounts is operated by employees from disparate agencies that essentially run them as they see fit.
Currently, there is no government-wide requirement that users use two-step verification to protect their accounts. There is no easy way for federal officials to know if an account was set up using an official government email address or someone's private gmail. And hundreds of government accounts still haven't been verified by the companies that host them.
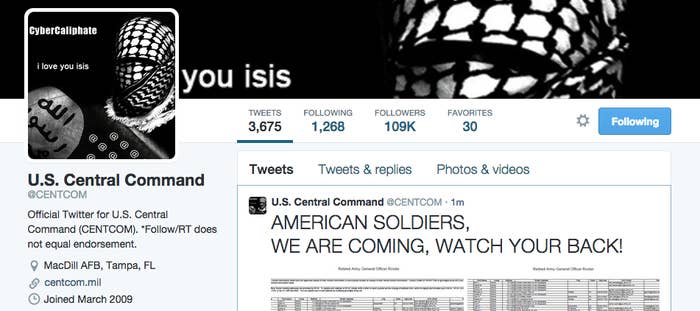
The lack of verification and security for accounts like this poses an obvious problem. Earlier this week, hackers took over social media accounts used by U.S. Central Command and turned them into propaganda tools for ISIS. Beyond revealing CENTCOM's vulnerability, the hack was more embarrassing than damaging — because the hackers made it very clear the account had been broken into.
Other hackers have been more nuanced. When the main Twitter account run by the Associated Press was attacked in 2013, hackers posted realistic reports of an explosion at the White House. The stock market dropped more than 100 points.
Social media is relatively new, especially in government years, and the feds have been slow to develop government-wide guidelines or rules on how to run social media accounts. After the CENTCOM hack, the General Services Administration is scrambling to shore up security standards — an effort that essentially entails telling employees to improve their social media security, but with few guarantees.
On Thursday, Justin Herman, the federal-wide social media program lead at GSA's Office of Innovative Technologies, hosted a hastily-assembled webinar entitled "How Government Can Prepare for and Respond to Social Media Hacks."
The webinar had the tone of an IT department demonstration at a large company. Herman, Lt. Anastacia Visneski, a digital media officer with the Coast Guard, and representatives from Facebook and the Twitter-access application HootSuite spoke over rotating slides about the need for difficult to break passwords, two-step verification, phishing scams, and Facebook settings — sometimes in the most basic terms.
"Just by doing a little bit of social engineering I can find out a lot about who you are. You know what your favorite football team is, what your dog's name is, all that stuff," said Sajji Hussain, a D.C.-based representative for HootSuite.
He described going to an agency's Twitter account, checking its list of followers, finding the feed's administrator by checking that list against LinkedIn or other social networks, and breaking into the account by simple guessing of passwords that are too simple.
"I go to your Twitter account and find you that you live in Pittsburgh, you love the Pittsburgh Steelers, and your dog's name is blah-blah," he said. "Now I can start guessing, right?"
Hussain suggested users find "complex passwords" that can't be guessed through research, and not to use the same login and password on all the social media accounts they use.
In bureaucracy as sprawling as the federal government, users can differ greatly when it comes to digital sophistication. And that can provide avenues for hackers. Visneski described the popularity of phishing scams that try to get a user to open an email attachment ("this picture of you partying in high school is going to get you fired" is especially good at caputring federal employees, she said.)
The GSA effort to upgrade social security faces some difficulties: GSA officials don't have the authority to enforce security rules, for one. Additionally, private-sector social media platform guidelines have sometimes made it tough for government workers to prevent the basic security systems in place that could prevent future CENTCOMs.
According to the government's social media registry, there are more than 5,000 social media accounts run by government agencies spread across dozens of familiar platforms like Twitter, Facebook, Flickr, Google+, Vimeo, and LinkedIn. Each agency runs its own, its own way, and often the most basic security precautions can be ignored for convenience's sake.
Current and former government social media users interviewed by BuzzFeed News after the CENTCOM Twitter hack described vastly different approaches to security. One former government employee said her agency didn't employ two-step verification on its social media accounts because it was too cumbersome to use the system with multiple social-media account administrators. Others described social media tools as being relegated to the bottom of the priority list, and control put in the hands of junior staffers.
In an email after the webinar, Herman wrote that it's not currently feasible for the federal government to have a central repository of social media account administrators and content.
"The government has thousands of social media accounts and thousands of public servants managing them, making a one-stop approach not only improbable but impractical — each agency must customize the guidance we have and lessons we learn for their own unique missions," he wrote. GSA's existing social media management structure — which includes a public-facing tool allowing internet users to determine if a purported government account is real or not — will "help inform and track adoption of protective advances like two-factor authentication with .gov or .mil email addresses and government devices including IPads and Android devices," Herman wrote.
GSA runs a digital government portal for federal employees that provides resources on all sorts of basic digital securiy etiquette. But in most cases, the social media experts in the government can only hope those resources are being used. Most of the time, it will take another high profile hack before they find out for sure.
The maturing of social media as a business tool can also provide more chances for security. Past rules at Facebook required users to use personal email accounts to register pages. That posed a problem for the security experts who say running government business through official .gov or .mil email addresses is the easiest way to prevent problems. Facebook has changed its rules as the site has become a key component of communication for private and public firms and agencies; in an email, a Facebook representative told BuzzFeed News nowadays "we actually prefer it," if government representatives use their work addresses to manage their work accounts.
Companies like Twitter and other social media outlets have begun adding two-step verification to their logins and creating systems that allow for multiple administrators to take advantage of them. Spreading news of those new security protocols and trying to get them adopted is now a main focus of the social media team at GSA.
They may have some new help in their efforts. The CENTCOM attack and the stepped-up concern over cybersecurity emanating from the White House after the recent attack on Sony Pictures could lead senior leaders at the Pentagon and civilian side of the government to pay much closer attention to how social media accounts are run, say people who work with government social media.
For now, concern over hacking is running high. Thursday morning, the Central Intelligence Agency posted a tweet in Russian quoting Boris Pasternak, the author of Dr. Zhivago.
"Just while we were talking, we got an email from the CIA," Herman said in the midst of the webinar. "They said, 'Hold on a second, will people think our account was hacked because we tweeted in a different language?'"
